Big Brother is Watching You – For Real (3)
Read the second part of the article
The Brain Project – This
area of study has received $100 million in funding via Obama’s ten-year
BRAIN Project, as well as a $1.3 billion commitment from Europe.
Concurrently, there is heavy military funding through agencies such as the Defense
Advanced Research Projects Agency (DARPA). This raises the question of transparency
when a “black budget” often justifies total secrecy in the name of
national security.

Neuroscientists Successfully Plant False
Memories – MIT neuroscientists have shown that they can plant false
memories. They also found that many of the neurological traces of these memories are
identical in nature to those of authentic memories. Most of the research in this
area currently revolves around how to induce and eliminate fear. The study also
provides further evidence that memories are stored in networks of neurons that form
memory traces for each experience we have. Scientists already know how to set off an
emotional response in combat veterans by simulating a specific set of frequencies
that have become associated with wartime experience.
Total Information Awareness
– Under the umbrella of a system known as Total Information
Awareness, DARPA spearheaded many of the surveillance programs abused by the
NSA. DARPA’s Total Information Awareness concept created a veritable
buffet of advanced surveillance and data mining programs, many of which ultimately
were folded into NSA’s PRISM. We now know that PRISM culled citizens’
personal data from companies like Microsoft, Google, and Facebook, and was later
leaked by whistleblower Edward Snowden.
Evidence Extraction and Link Discovery
program (EELD) – Sole purpose is to gather as much information about
both terror suspects and average American citizens as possible, using phone records,
computer searches, credit card receipts, parking receipts, books checked out of the
library, films rented, and more. Goal is to assess megadata on 285 million people a
day in real-time.
Scalable Social Network Analysis (SSNA)
– Program monitors telephone calls, conference calls, and ATM
withdrawals… also sought to develop a far more invasive surveillance
technology.
Activity Recognition and Monitoring
(ARM) – With England’s CCTV surveillance cameras as a model,
ARM created a massive database of people going about their everyday lives. Using
advanced facial recognition software, the program highlighted any behavior that was
outside the realm of a preprogrammed “ordinary,” the definition of which
remains classified.
Deep Exploration and Filtering of Text
(DEFT) – Operating on a $28 million dollar budget, this program
utilizes advanced computer algorithms to analyze text-based messages in all shapes
and forms, from text messages to reports, with the aim being to comprehend
“implied and hidden meanings through probabilistic
inference.”
Nexus 7 – With a
classified budget, this particularly program studies and tracks social network
content. First used in Afghanistan in a defense capacity, when aimed at domestic
networks the use of the program is a mystery.
Narrative Networks Program
– Developed classified techniques used to manipulate trust in humans. For its
Narrative Networks (N2) program, DARPA collaborated with a CIA agency called the
Intelligence Advanced Research Projects Agency (IARPA) to develop methods of
overwriting messages in the human mind. The program was described as having two
parts: first, to understand what happens in the human mind when someone sees or
hears a message; second, to figure out how to control how the brain interprets the
message.
In-Q-Tel Projects
Recorded Future – Using
what they call a “Temporal Analytics Engine,” Recorded Future
(RF) provides forecasting and analysis tools to help analysts predict future events
by scanning sources on the Internet, and extracting, measuring, and visualizing the
information to show networks and patterns in the past, present, and future. As of
2015 the engine was described as “Web Intelligence Engine Visible
Technologies” – social media monitoring.
Digital Reasoning – Since
2012, the firm has sold its Synthesys software to banks and hedge funds,
including UBS and Point72 Asset Management. Financial institutions use
Synthesys to scan internal e-mails within a given company in search of
unfamiliar patterns between employees, in terms of word-specific content, frequency
and interpersonal connections. The aim is to predict fraud before it occurs.
Palantir – Palantir
Technologies, Inc. is a private American software and services company, specializing
in data analysis. The company is known for two software projects in particular:
Palantir Gotham is used by counter-terrorism analysts at offices in the United
States Intelligence Community and United States Department of Defense, fraud
investigators at the Recovery Accountability and Transparency Board, and cyber
analysts at Information Warfare Monitor.

CallMiner – Phone speech
analytics software.
MASINT – Remote tracking,
surveillance, and extraction of brain-waves typifying thought-forms, emotional
states, analytic mind states, and others.
Mohomine mohoClassifier –
Organizes mass data.
3VR – 3VR Inc. develops
software enabling organizations to mine data from video. 3VR works with leading
banks, governments, law enforcement and retailers at the moment.
Adaptx – Creates digital
pens that speed up field data collection.
Basis Technology –
Synthesizes the foreign chatter and provides software for text analytics in over
twenty languages. They work primarily in applied natural language processing,
deriving meaning from the ways people actually use language.
Cloudera – Large-scale
data storage. Cloudera Enterprises is one of the most cost-effective ways for
companies to securely carry out large-scale data analysis and storage.
FireEye – FireEye is one
of the most advanced cybersecurity firms and specializes in protecting against
botnet attacks and also works to combat the malware that brings computers into the
network.
The Ember Corporation –
Ember Corporation focuses on developing networking systems that simplify wirelessly
networking low-power products. They’re focused on smart energy, remote
monitoring, and remote control uses of their tech.
Infinite Z – Virtual-
holographic simulation a reality through an interactive 3D environment.
OpenSpan – Makes software
that enables organizations to see exactly what employees are doing on their
computer: what programs they’re using, what progress they’re making,
etc.
Seventh Sense – Develops
health monitoring products that interface with human skin.
Sonitus Medical – Makes a
hearing system that transmits sound imperceptibly through the mouth. The SoundBite
hearing system plays off the principle of bone conduction to transmit audial
messages. A nearly invisible in-the-mouth hearing and communication platform is
non-invasive and connects directly to the inner ear, allowing the user to hear
transmitted messages through their skull.
Spotter RF – Makes super-
powerful radars in a handheld form that can track a person walking anywhere within a
148 acre space, and it’s handheld.
Visible Technologies –
Extracts business solutions from social media chatter with software that allows
users to extract business value from social communities, and also give customer
insights for brands online.
Walleye – Makes handheld
devices that can see into and through solid objects.
In-Q-Tel and DARPA Mind Control
Programs
Real-time Contextual Overlays for Live
Streams – A system and method for contextualizing and live-updating
overlay data for live media streams. Overlays can be generated in real-time and in
response to live events. (patent US 20130311595 A1 November 21, 2013.
Google Inc.)
Method and Apparatus for Remotely
Determining Emotional States – A waveform energy having a
predetermined frequency and intensity is generated and wirelessly transmitted
towards a subject. Physiological or physical parameters of blood pressure, pulse
rate, pupil size, respiration rate and perspiration level are measured for
evaluating criminal intent in security sensitive areas. (patent US 5507291
A – April 5, 1994)
Sounds of Silence: The Silent Subliminal
Presentation System (SSPS) – Silent Subliminal Presentation System
was developed for commercial use in 1992. A silent communications system in which
nonaural carriers, in the very low (ELF) or very high audio-frequency (VHF) range or
in the adjacent ultrasonic frequency spectrum are amplitude – or frequency-
modulated with the desired intelligence and propagated acoustically or
vibrationally, for inducement in to the brain, typically through the use of
loudspeakers, earphones, or piezoelectric transducers. The modulated carriers may be
transmitted directly in real time or may be recorded and stored on mechanical,
magnetic, or optical media for delayed or repeated transmission to the listener.
(US Patent 5,159,703)
Flame – The program is
able to turn on a target’s web cam and record video remotely and without
detection.
Multidisciplinary Research Program of the
University Research Initiative (MURI) – Recognizes/predicts social
contexts, relationships, networks, and intentions from social media, taking into
account non-verbal communication such as gestures, micro-expressions, posture, and
latent semantics of text and speech. Creates algorithms for prediction and
collection of latent signals and their use in predicting social information.
Beware – Analyses
people’s social media activity, property records, the records of friends,
family or associates, among other data, to assign suspects a so-called
“threat-score.” That “threat-score” can
then be used by police to pre-judge if a suspect is going to be dangerous, and to
adapt their approach accordingly.
Iraqi Silent Sound Program
– US Psy-Ops teams set up FM transmitters, utilizing Iraqi frequencies and
overpowered the local station. Along with patriotic and religious music, PsyOps
transmitted “vague, confusing and contradictory military orders and
information.” A sophisticated electronic system designed to
‘speak’ directly to the consciousness of the listener; to alter and
entrain his brainwaves, to manipulate his brain’s electroencephalographic
(EEG) patterns and thus artificially implant negative emotional states –
feelings of intense fear, anxiety, despair and hopelessness were created in the
Iraqi troops. This effective subliminal system implants emotions in the minds of the
targeted subject.
Nervous system manipulation by
electromagnetic fields from monitors – US Patent and Trade
Office, Patent #6,506,148 on subliminal behavior modification, 1/14/2003,
United States Patent 6,506,148, Loos, January 14, 2003.
Abstract: “It is possible to manipulate the nervous
system of a subject by pulsing images displayed on a nearby computer monitor or TV
set. For the latter, the image pulsing may be imbedded in the program material, or
it may be overlaid by modulating a video stream. Physiological effects have been
observed in a human subject in response to stimulation of the skin with weak
electromagnetic fields that are pulsed with certain frequencies near 1/2 Hz or 2.4
Hz, such as to excite a sensory resonance.
Many computer monitors and TV tubes, when
displaying pulsed images, emit pulsed electromagnetic fields of sufficient
amplitudes to cause such excitation. It is therefore possible to manipulate the
nervous system of a subject by pulsing images displayed on a nearby computer monitor
or TV set. For the latter, the image pulsing may be imbedded in the program
material, or it may be overlaid by modulating a video stream, either as an RF signal
or as a video signal.
The image displayed on a computer monitor may
be pulsed effectively by a simple computer program. For certain monitors, pulsed
electromagnetic fields capable of exciting sensory resonances in nearby subjects may
be generated even as the displayed images are pulsed with subliminal intensity.
Inventors: Loos; Hendricus G. (3019 Cresta Way, Laguna Beach, CA 92651), Appl. No.:
872528 Filed: June 1, 2001.”
Other DARPA/In-Q-Tel
Programs
Total Information Awareness
– Under the umbrella of a system known as Total Information
Awareness, DARPA spearheaded many of the surveillance programs abused by the
NSA. DARPA’s Total Information Awareness concept created a veritable
buffet of advanced surveillance and data mining programs, many of which ultimately
were folded into NSA’s PRISM. PRISM culled citizens’ personal data from
companies like Microsoft, Google, and Facebook.
PRISM – A clandestine
national security electronic surveillance program operated by the United States
National Security Agency which can target customers of participating corporations
outside or inside the United States.
Sounds of Silence – The Silent
Subliminal Presentation System was developed for commercial use in 1992. A
silent communications system in which non-aural carriers, in the very low (ELF) or
very high audio-frequency (VHF) range or in the adjacent ultrasonic frequency
spectrum are amplitude – or frequency- modulated with the desired intelligence
and propagated acoustically or vibrationally, for inducement in to the brain,
typically through the use of loudspeakers, earphones, or piezoelectric transducers.
The modulated carriers may be transmitted directly in real time or may be recorded
and stored on mechanical, magnetic, or optical media for delayed or repeated
transmission to the listener. US Patent 5,159,703.
Turbulence –
Turbulence is a National Security Agency information-technology project
started circa 2005. It was developed in small, inexpensive “test” pieces
rather than one grand plan like its failed predecessor, the Trailblazer
Project. It also includes offensive cyberwarfare capabilities, like injecting
malware into remote computers.
Tailored Access Operations
– Intelligence-gathering unit of the NSA that is capable of harvesting
approximately two petabytes of data per hour.
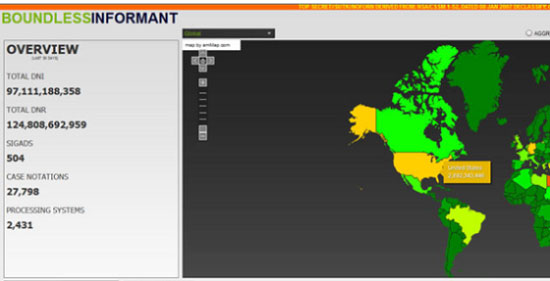
Boundless Informant – A
system deployed by the NSA to analyze global electronic information. In March 2013,
Boundless Informant gathered 14 billion data reports from Iran, 6.3 billion from
India, and 2.8 billion from the United States.
Bullrun – A highly
classified National Security Agency program to preserve its ability to eavesdrop on
encrypted communications by influencing and weakening encryption standards, by
obtaining master encryption keys, and by gaining access to data before or after it
is encrypted either by agreement, by force of law, or by computer network
exploitation (hacking).
Carnivore – A system
implemented by the Federal Bureau of Investigation that was designed to monitor
email and electronic communications.
DCSNet – The Federal
Bureau of Investigation’s point-and-click surveillance system that can perform
instant wiretaps on any telecommunications device located in the US.
Fairview – A mass
surveillance program directed at foreign mobile phone users.
ICREACH – Surveillance
front-end GUI that is shared with 23 government agencies, including the CIA, DEA,
and FBI, to search illegally collected personal records.
Magic Lantern – A
keystroke logging software deployed by the FBI in the form of an e-mail attachment.
When activated, it acts as a Trojan horse and allows the FBI to decrypt user
communications.
Main Core – A personal and
financial database storing information of millions of U. S. citizens believed to be
threats to national security. The data mostly comes from the NSA, FBI, CIA, as well
as other government sources.
MAINWAY – A NSA database
containing metadata for hundreds of billions of telephone calls made through the
four largest telephone carriers in the United States.
MUSCULAR – Overseas
wiretapping of Google’s and Yahoo’s internal networks by the
NSA.
MYSTIC – Is a voice
interception program used by the National Security Agency.
Room 641A – A
telecommunication interception facility operated by AT&T for the U.S. National
Security Agency.
Sentry Eagle – It monitors
and attacks an adversary’s cyberspace through capabilities include SIGINT,
Computer Network Exploitation, Information Assurance, Computer Network Defense,
Network Warfare, and Computer Network Attack. The efforts included weakening U. S.
commercial encryption systems.
Special Collection Service
– A black budget program that is responsible for “close
surveillance, burglary, wiretapping, breaking and entering.” It employs
covert listening device technologies to bug foreign embassies, communications
centers, computer facilities, fiber-optic networks, and government
installations.
Terrorist Finance Tracking
Program – A joint initiative run by the CIA and the Department of the
Treasury to access the SWIFT (Society for Worldwide Interbank Financial
Telecommunication) transaction database as part of the Bush administration’s
“Global War on Terrorism.”
Multi-state Anti-Terrorism Information
Exchange (MATRIX) – A data mining system originally developed for the
Florida Department of Law Enforcement.
Insight Program – It
detects threat networks, irregular warfare, and terrorist operations by combining
intelligence information from imaging sensors, crowd-source and other social network
or text-based sensors, as well as from other sources for further analysis. Develops
integrated human/machine reasoning into intelligence equipment to encompass operator
knowledge and reasoning when dealing quickly with complex data from many different
sensors.
EM Fields and Hidden Symbols
– Uses techniques to incept thoughts and ideas into the consciousness. Once a
consciousness has been programed with the memory patterns, words and symbols can
trigger the programing without the need of the original device.
Narrative Networks Program
– Developed classified techniques used to manipulate trust in humans. For its
Narrative Networks program, DARPA collaborated with a CIA agency called the
Intelligence Advanced Research Projects Agency (IARPA) to develop methods of
overwriting messages in the human consciousness.
Mind Control Project –
Remotely disrupts political dissent and extremism by employing
“Transcranial Magnetic Stimulation” (TMS) in tandem with
sophisticated propaganda based on this technology. TMS stimulates the temporal lobe
of the brain with electromagnetic fields. This research aims to stop individuals
from thinking certain thoughts and make others believe things they normally would
not believe. This research is being conducted by The Center for Strategic
Communication at ASU and is entitled “Toward Narrative Disruptors and
Inductors: Mapping the Narrative Comprehension Network and its Persuasive
Effects.” Mechanical disruptions of narrative processing may be,
ultimately, replicated through targeted strategic communication campaigns that
approximate the narrative disruptions induced via magnetic stimulation. MIT
neuroscientists have shown that they can plant false memories. Most of the research
in this area currently revolves around how to induce and eliminate fear.
yogaesoteric
March 12, 2020
